Virtualizing your Linux Firewall
From WBITT's Cooker!
m (→The Linux Physical Firewall) |
(→Disadvantages) |
||
| (47 intermediate revisions not shown) | |||
| Line 13: | Line 13: | ||
License: Copyright (c) 2011 by Muhammad Kamran Azeem. Permission to copy, distribute (sell or giveaway) and translate, provided you retain the name of the original author. | License: Copyright (c) 2011 by Muhammad Kamran Azeem. Permission to copy, distribute (sell or giveaway) and translate, provided you retain the name of the original author. | ||
| - | Synopsis: This paper discusses the concept of running your Linux Firewall as a Virtual Machine. | + | Synopsis: This paper discusses the concept of running your Linux Firewall as a Virtual Machine, and provides a design guide-line to do so. |
==Introduction== | ==Introduction== | ||
In today's IT world, almost all IT managers know what exactly it means for the business, when a firewall is down. When this alarm is raised, it is just like the fire alarm. All of a sudden there is immense panic, there are question marks on everyone's face, productivity is halted, and people rush to see, who reaches to the coffee machine first; except the IT staff. To the IT staff, it seems like hell has broken loose. The managers of all level, almost all at once, start yelling at the IT staff, to get the network back up as soon as possible. It is quite a scene! | In today's IT world, almost all IT managers know what exactly it means for the business, when a firewall is down. When this alarm is raised, it is just like the fire alarm. All of a sudden there is immense panic, there are question marks on everyone's face, productivity is halted, and people rush to see, who reaches to the coffee machine first; except the IT staff. To the IT staff, it seems like hell has broken loose. The managers of all level, almost all at once, start yelling at the IT staff, to get the network back up as soon as possible. It is quite a scene! | ||
| - | For people using hardware based firewalls of prominent brands, like Cisco PIX, Juniper NetScreen, or SonicWall, etc, this can actually mean a lot of downtime. Especially in cases when the firewall device has actually got burnt because of some power surge. They would have to wait for a replacement unit to arrive. In case the firewall was cracked, by a cracker, it would again mean a lot of downtime, as the firewall device has to be re-configured, probably from a clean backup, if | + | For people using hardware based firewalls of prominent brands, like Cisco PIX, Juniper NetScreen, or SonicWall, etc, this can actually mean a lot of downtime. Especially in cases when the firewall device has actually got burnt because of some power surge. They would have to wait for a replacement unit to arrive. In case the firewall was cracked, by a cracker, it would again mean a lot of downtime, as the firewall device has to be re-configured, probably from a clean backup, if there was any! |
Normally there is only one such device in an environment, because they are pretty expensive. And, as noted above, a burnt device, or any component of it, such as a WAN port, can seriously cripple your business to a complete halt. | Normally there is only one such device in an environment, because they are pretty expensive. And, as noted above, a burnt device, or any component of it, such as a WAN port, can seriously cripple your business to a complete halt. | ||
| - | Many people consider Cisco PIX as the <i>Holy Grail</i> of firewalls. Same is the general point of view about other hardware-based/proprietary firewalls, such as Juniper NetScreen, SonicWall, CheckPoint, NetGear, etc. There is nothing much you can do "different", with the so-called hardware/proprietary firewalls, compared to what you can do with Linux based firewalls. One of the popular strategy used by the sales people | + | Many people consider Cisco PIX (Private Internet eXchange), as the <i>Holy Grail</i> of firewalls. Same is the general point of view about other hardware-based/proprietary firewalls, such as Juniper NetScreen, SonicWall, CheckPoint, NetGear, etc. There is nothing much you can do "different", with the so-called hardware/proprietary firewalls, compared to what you can do with Linux based firewalls. One of the popular strategy used by the sales people / vendors is to create <i>Fear, Uncertainty and Doubt</i>,(FUD), about low cost Linux firewalls, in the minds of customers. When they are successful in doing so, they (sales people) move to the next step, and convince their customers to purchase the ultra expensive firewall from brand X. The interesting point is, that even the IT managers at the customer side, do not resist in such purchases. Because, they "feel secure" by merely purchasing a branded product, and don't want to take any risk by saying "No". Once the brand X firewall product is acquired by the customer, it is placed on the network, without a well thought out configuration/plan. In a hurry to brag <i>"I have configured the brand X firewall and placed it in production in 30 minutes"</i>, the IT staff, constantly under the influence of the brand X name/reputation, puts something on the network, which is, (a) not well configured, (b) no-body understands it well enough (c) is outrageously expensive, and (d) was not required in the first place. Most of the time it ends up like <i>buying a rocket launcher to kill a fly</i>. |
| - | In this paper we would discuss the possibility of using Linux based firewalls, running as virtual machines, on a XEN | + | In this paper we would discuss the possibility of using Linux based firewalls, running as both physical/hardware appliances; and as virtual machines, on a XEN / KVM host. We would also show, how this (firewall virtualization) can be achieved. |
==The Physical Firewall== | ==The Physical Firewall== | ||
| + | ===The hardware-based branded firewalls=== | ||
| + | To explain this topic, we would use an example from the real world; the most commonly known firewall device, <i>Ciso PIX</i>. It would be interesting for many to know that the processors used in Cisco PIX firewalls were Intel Celeron, Intel PIII, and AMD's Am5x86. The chipsets used on the mainboards of these firewalls were Intel 440BX and AMD's SC520 chip-sets. And the RAM ranged between 16 MB to 512 MB (to 1 GB). [Reference: http://en.wikipedia.org/wiki/Cisco_PIX#Description_of_hardware]. | ||
| + | |||
| + | Also, if you are thinking of buying any of the Cisco PIX firewall, you should note that in 2008 Cisco announced EOS (End of Sale) for Cisco PIX series. It is replaced with a newer "Adaptive Security Appliance", or ASA for short, introduced in 2005. Cisco ASA 5500 Series replaced three lines of Cisco security products: PIX, IPS and VPN. Models such as Cisco PIX 501 or Cisco PIX 515 are not produced or sold any more. Cisco PIX "technology" is still sold in a blade form, as a Firewall Services Module (FWSM) into Cisco's Catalyst 6500 Switches and 7600 Series Routers. | ||
| + | |||
| + | You can still purchase the older/used PIX devices/models for anywhere between $500 to $5000, depending on model, specifications, and of-course, the quality. | ||
| + | |||
| + | You would notice that even in newer Cisco security products (ASA 5500 series), the processors used are as low as 500 MHz and as high as 2.6 GHZ, with processor types including Intel P4, Celeron and AMD Opeteron. The medium range products in ASA 5500 series have RAM range between 256 MB and 1 GB. The higher end models have 4GB to 12 GB of RAM. [ Reference: http://en.wikipedia.org/wiki/Cisco_ASA] | ||
| + | |||
| + | The Cisco PIX firewall may been one of the best seller in the enterprise firewall areana, its ISO command line interface was never liked (and never fully understood) by the general (non-Cisco) IT staff. Same is almost true for all the branded/proprietary hardware firewalls out there. | ||
| + | |||
| + | Below are few more examples of hardware based firewalls: | ||
| + | |||
| + | * Netgear FVX538 Prosafe Dual WAN VPN FIREWALL WITH 8-PORT 10/100 SWITCH | ||
| + | ** Processor: 533 MHz Intel XScale IXP425 | ||
| + | ** Memory: 32 MB flash, 64 MB DRAM | ||
| + | ** Encryption accelerator: Cavium Processor up to 60+ Mbps (3DES+SHA-1) encryption | ||
| + | |||
| + | * Netgear FVS124G ProSafe Dual WAN VPN Gigabit Firewall | ||
| + | ** Processor: 200 MHz 32-bit RISC | ||
| + | ** Memory: 4MB Flash, 16MB DRAM | ||
| + | |||
| + | Most customers/users only look at the "initial" price of the firewall. In most of the cases, the hardware based firewalls from almost all prominent vendors provide limited services against the initial payment; and are sort of locked down to a small number of users/sessions/ports. These vendors charge extra, in the name of licenses, to allow more users traffic (sessions) to pass through the firewall. Normally the vendors also charge yearly subscription fee for premium services, such as Content Filtering, AntiVirus, AntiSpam, VPN, etc. This normally totals up to a larger sum, drawing out more money from the company, compared to what was anticipated in the beginning. | ||
| + | |||
| + | Readers might be wondering, <i>"What is it, in a hardware appliance firewall, which makes is so costly?"</i> The answer is, that the hardware firewalls have custom designed hardware. They may be using a standard Intel or AMD processor, but the other components would be built-in on the main-board. Network cards, which are the most important component/feature of a firewall device, are slimmed down, and are provided as network interfaces. There are also certain components, which you will not find in such an appliance. For example. You would not find a VGA, or Keyboard and mouse ports on your appliance. Such custom designs provide serial interfaces / console ports, which can be connected to using a null-modem cable, etc. You will find a minimum of two network ports on the most basic firewall. One for Internet (Red Zone), and the other for LAN (Green zone). The newer designs include several network ports; some of them are additionally there to provide facility to configure DMZs (Orange Zone). Also, the newer firewalls devices/appliances have built in Wireless device, providing a fourth configurable zone (Blue Zone). Instead of using a hard disk for storage, you will find small sized flash disks. The OS is proprietary with a minimal user interface, normally through command line. In newer designs, firewall vendors have started providing secure web interface to configure the device. The operating system is minimalistic in nature, and does not consume much RAM too. It therefore does not "require" extra RAM to function. And above all, all components are enclosed in a small (slick) box, which does not take up much desk/rack space. This all is what makes such devices known as "hardware based firewalls" or "branded firewalls". | ||
| + | |||
| + | ===The hardware-based Linux firewalls=== | ||
Fundamentally, any hardware-based firewall is a collection of hardware and software components. A hardened Linux box, with enough resources, used "solely" in a firewall role, can confidently be termed as a hardware firewall; and it can compete with any branded firewall you can throw against it. Besides, it is the configuration, which makes a firewall strong; not it's brand. | Fundamentally, any hardware-based firewall is a collection of hardware and software components. A hardened Linux box, with enough resources, used "solely" in a firewall role, can confidently be termed as a hardware firewall; and it can compete with any branded firewall you can throw against it. Besides, it is the configuration, which makes a firewall strong; not it's brand. | ||
| - | + | A modern day PC is much more powerful than what is described above. A cut down version / minimal install of Linux OS of your choice, on a commodity off the self (COTS) PC, can essentially turn it into a firewall, <i>more powerful</i> than the Cisco PIX. The only (non-serious) disadvantage may be the dimensions of your Linux box. The physical dimensions of an ordinary desktop computer takes up a lot of space on the desk, floor or rack. (It may look ugly too!). | |
| - | + | Linux and its command line interface is very well understood by almost all Open Source enthusiasts. Plus, there is a lot of documentation/help out there on the Internet. Thus, using Linux as the OS for your firewall proves to be an excellent choice. Linux OS is normally available free of cost, so the only direct costs are the hardware costs for such a firewall. The cost of a custom made (Linux) firewall device, range between $200-$900, depending on your requirements. Still it is much lower a price compared to $5000+ for a branded firewall. A Linux based hardware firewall can offer almost all services which any other type of firewall can offer. It is just the matter of adding the right modules and software pieces to it. For example, a basic <i>Packet Filtering Linux Firewall</i> can work as a <i>Stateful Firewall</i>, merely by adding a connection tracking kernel module, and some configuration. The following non-exhaustive list provides an insight into what all can be accomplished by using Linux OS and it's free tools. | |
| - | + | ||
* Packet Filtering: IPTables | * Packet Filtering: IPTables | ||
| Line 47: | Line 73: | ||
* .... and more. | * .... and more. | ||
| - | You can have one "thick" Linux firewall, in your network, by having all of the security services on one physical machine, which is an advantage in it's own. (You will | + | You can have one "thick" Linux firewall, in your network, by having all of the security services on one physical machine, which is an advantage in it's own. (You will not experience virtualization overheads, explained later). There are many Open Source firewall projects, which are reliable and robust; and are being used in production networks all over the world. Shorewall, SmoothWall, Untangle, Endian, IPCop, CopFilter and pfSense are few excellent firewall solutions , usable in environments ranging from SOHO, to enterprise. |
| - | To give you an idea of the hardware, and related costs, consider | + | To give you an idea of the hardware, and related costs, consider a normal PC, with P4 or higher processor, 800 MHz or higher speed, 256 MB or more RAM, and 40 GB or more disk space, with at least 2 Network cards. A PC with such hardware specifications is an ideal candidate for a firewall device/appliance. 800 MHz processor is good enough to handle about 50 users. The more users you have, the more powerful processor you need, (along more RAM), because the primary function of any firewall (packet filtering), eats the most of the CPU. If you also need to provide VPN, you should consider a processor with speed in excess of 1.6 GHz. As noted above, the cost of such custom made (Linux) firewall device, range between $200-$900, depending on your requirements. Again, it is much lower a price compared to $5000+ for a branded firewall. |
| - | <b>Note: </b>While power is a concern for any equipment you are running, don't fall into the trap of using Atom processors, just for the reason that they consume low power. Atom processors do not have enough compute power to act as an efficient firewall. | + | <b>Note: </b>While power is a concern for any equipment you are running, don't fall into the trap of using Atom processors, just for the reason that they consume low power. Atom processors do not have enough compute power to act as an efficient firewall for a larger network. |
| - | While this paper is about Virtualizing your firewalls, make no mistake in understanding that a physical | + | While this paper is about Virtualizing your firewalls, make no mistake in understanding that a physical/hardware firewall, will always outperform a virtual one. This is because there are no virtualization overheads, nor any infrastructure complexities. If you can afford the cost of extra hardware, the power consumption, and the configuration time, we recommend that you use a physical (Linux) firewall instead of setting up a virtual one. It is highly recommended to have redundancy of the equipment, to provide business continuity. Linux firewalls are very efficient and secure, (if configured correctly), economical, and affordable, compared to their branded counter parts. There is no reason, why you should not use one. |
==The Virtual Firewall== | ==The Virtual Firewall== | ||
| - | + | In this paper, we try to explain, how <i>compartmentalized security model</i> can be implemented, by running most of the services listed above as separate "thin" virtual machines, on a single physical server. And that for the sake of ensuring business continuity, a copy of all VMs can be kept on a second (in-expensive) physical machine. In case of hardware failure, the firewall and it's related components can be run from this second machine, without significant downtime. | |
| - | Thus, instead of running one "thick" physical machine as firewall, we can run multiple thin "virtual | + | Thus, instead of running one "thick" physical machine as firewall, we can run multiple "thin" virtual machines. Below are few of advantages and disadvantages of running your firewall as a VM. |
===Advantages=== | ===Advantages=== | ||
| - | * Compartmentalized Security: | + | * Compartmentalized Security: One VM can be setup to act as a firewall, while the other VM can run services like WebCache, DNS, etc. If a cracker gains access to the cache server, that is the only VM affected. Your main firewall will still continue to handle traffic. |
| - | * No single point of failure: If | + | * No single point of failure: If one VM's disk is full, with logs, etc, it will be the only VM, which will fail, or will not respond. The other VM will keep functioning. |
| - | * Service/VM Load Balancing: If | + | * Service/VM Load Balancing: If the VM running the WebCache/content-filtering services is taking too much physical resources of the physical host, that VM can be moved to another physical machine on the network. |
| - | * COTS/in-expensive hardware: This | + | * COTS/in-expensive hardware: This gives you the (financial) freedom to have multiple physical machines in stock. In case a hardware failure occurs, the second physical machine can be quickly setup to run these VMs and the services they offer. |
| + | * Cloud capable: Virtual firewalls can prove really useful in environments which are heavily virtualized, such as <i>Cloud</i>. Several virtual firewalls can exist within a larger virtual network, serving different departments, or different customers. | ||
| + | * Support: Normally, the first question asked about a product, before it's formal review is: "Who will provide support for this?" . In case of the in-expensive Linux firewalls (both Physical and Virtual), explained in this paper, the support is expected from the particular distribution vendor who's Linux flavour is installed on the firewall. This is true for almost all commercial Linux distributions. However, if you are running free distributions, such as Debian, CENTOS, Fedora, Ubuntu, etc; you should expect the support from your Linux administrators. In 99% of cases, it is the Linux system admins in the IT staff, who propose, and often implement such technologies without external help. As you would be noticing that the free Linux distributions cannot be directly asked to provide support. However, they all have bug tracking / issue tracking systems, which are actively monitored by the back end developers. Also, there are "support companies" active in this field, who provide commercial/professional support for these free Linux distributions. | ||
===Disadvantages=== | ===Disadvantages=== | ||
| - | * Virtualization overhead: Virtualization means, that there must be a Hypervisor | + | * Virtualization overhead: Virtualization means, that there must be a Hypervisor, to host all virtual machines. The hypervisor itself consumes certain amount of resources, mainly RAM, and CPU. If the size of RAM is already low/small on the physical host, there is little left for VMs to run efficiently. This is equally true for any computer system which is low on CPU power, and in some cases, disk-space. |
| - | * Extra complexity: Virtualization introduces extra level of complexity in the infrastructure/network. The administrator has not only to take care of the physical machine and it's network connections, for example; he also has to take care of the VMs, the virtual networks inside the machine, and a keep an eye on the resource utilization. | + | * Extra complexity: Virtualization introduces extra level of complexity in the infrastructure/network. The administrator has not only to take care of the physical machine and it's network connections, for example; he also has to take care of the VMs, the virtual networks inside the machine, and a keep an eye on the resource utilization. |
| + | * Requirement of additional IPs: All virtual and physical network interfaces (of physical and virtual machines) need to have IPs assigned to them. Thus there is a requirement of additional IPs. | ||
| - | <b>Note:</b> If you do not plan to host many thin VMs on your physical host, or if you are low on hardware resources, you can simply let go of the idea of Virtualizing your firewall, and just go ahead with a physical (Linux based) firewall. One of the key principals of security is to keep your system "managed" and "manageable". The moment the complexity of any system becomes un-manageable, it develops vulnerabilities, which can later be exploited. Thus, simplicity must be a fundamental idea when designing any system; and firewalls are not an | + | <b>Note:</b> If you do not plan to host many thin VMs on your physical host, or if you are low on hardware resources, you can simply let go of the idea of Virtualizing your firewall, and just go ahead with a physical (Linux based) firewall. One of the key principals of security is to keep your system "managed" and "manageable". The moment the complexity of any system becomes un-manageable, it develops vulnerabilities, which can later be exploited. Thus, simplicity must be a fundamental idea when designing any system; and firewalls are not an exception. |
==Designing a Virtual Firewall System== | ==Designing a Virtual Firewall System== | ||
===Scenario=== | ===Scenario=== | ||
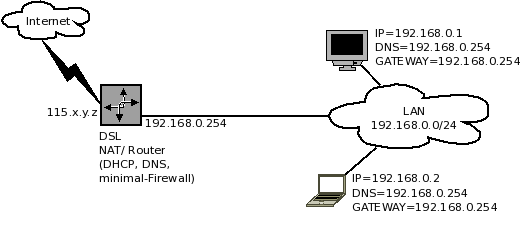
| - | While designing a Virtual Firewall System, and it's components, you should first | + | While designing a Virtual Firewall System, and it's components, you should first identify the tasks it will be performing for your network. In this document, we have the assumption, that you are placing such a firewall between Internet and your LAN users, to protect them from each other. Internet is reachable through a DSL router, which has a public IP. The LAN interface of this DSL router is connected to a switch, to which all of your users are connected to. The DSL router, is providing DHCP, DNS and NAT services to your users. We will also assume that the DSL Router has a built-in firewall, which no-one has bothered to configure for your setup, or has very limited firewall features. The users need to be protected (from the Internet), and also provided with some basic services, such as a cache server. The Internet needs to be protected from the LAN users, such as, any virus infected PC should not send floods of emails/spam through your DSL router, towards the internet. Thus a need to place a Linux firewall in between. First, here is how the setup looks like when there is no firewall placed on the network. |
[[File:Firewall-Typical-DSL-Setup-01.png|frame|none|alt=|Figure 1: A typical set up without a firewall.]] | [[File:Firewall-Typical-DSL-Setup-01.png|frame|none|alt=|Figure 1: A typical set up without a firewall.]] | ||
| Line 87: | Line 116: | ||
We have used XEN as an example to create a Virtual Firewall System. The design is shown in the diagram below. You can also use KVM, if you want to. | We have used XEN as an example to create a Virtual Firewall System. The design is shown in the diagram below. You can also use KVM, if you want to. | ||
| - | [[File:Firewall-Virtualization- | + | [[File:Firewall-Virtualization-03-70p.png|frame|none|alt=|Figure 3: A Virtual Firewall System. Two VMs inside the physical machine.]] |
| - | Larger version of this diagram is | + | Larger version of this diagram is available at: http://cooker.techsnail.com/images/d/dd/Firewall-Virtualization-03.png |
The diagram is explained as following: | The diagram is explained as following: | ||
| Line 95: | Line 124: | ||
# peth0 and peth1 are the physical network cards of the physical machine. | # peth0 and peth1 are the physical network cards of the physical machine. | ||
# pCPU = Physical CPU, pRAM = Physical RAM, and pDISK = Physical Disk | # pCPU = Physical CPU, pRAM = Physical RAM, and pDISK = Physical Disk | ||
| - | # The grey box inside the big white box is supposed to be Domain-0. In a perfect diagram, | + | # The grey box inside the big white box is supposed to be Domain-0. In a perfect diagram, all virtual machines should be drawn outside the grey box. You can still assume the grey box to be Domain-0 for ease of understanding. For better understanding of this point, check the XEN network concepts explained in this article: [Reference: http://cooker.techsnail.com/index.php/Virtualization-XEN] |
| - | # xenbr0 is a software bridge | + | # xenbr0 is a software bridge, connected to the physical LAN 192.168.0.0/24, through peth0. The virtual network card eth0 of Domain-0 (XEN host) is connected to this bridge on port vif0.0 . |
| - | # xenbr1 is a software bridge | + | # xenbr1 is a software bridge, connected to the physical LAN 192.168.1.0/24, through peth1. The virtual network card eth1 of Domain-0 (XEN host) is connected to this bridge on port vif0.1 . |
| - | # VM1 is | + | # VM1 is XEN Domain-1 (dom-U), and is configured to act as a firewall. |
| - | # Notice the change in IP assignment in Figure 3, compared to Figure 2. The IP used as GATEWAY by the LAN users, is now assigned to eth1 of VM1 (firewall), instead of | + | # VM2 is XEN Domain-2 (dom-U), and is configured to run WebCache (squid), and DNS (BIND) services. |
| - | # VM1 runs in the | + | # Notice the change in IP assignment in Figure 3, compared to Figure 2. The IP used as GATEWAY by the LAN users, is now assigned to eth1 of VM1 (firewall), instead of eth1 of the physical host. |
| - | # VM2 runs in the | + | # VM1 runs in the Firewall role. It has two interfaces, each connecting to a different bridge, (xenbr0 and xenbr1), and thus essentially becomes/acts-as a router. The eth0 interface of VM1 is connected to vif1.0 port on xenbr0. The eth1 interface of VM1 is connected to vif1.1 port on xenbr1. VM1 runs DHCPD service listening/serving on it's eth1 interface. |
| - | # VM2 (webcache) <i>can</i> connect to xenbr0 through its network interface on the left (eth0). (This is the debatable part mentioned in the previous point; the link | + | # VM2 runs in the WebCache role, and also provides caching DNS services, using BIND (caching-nameserver). It is running Squid on port 3128. It also has two interfaces(, which may be debatable). The right hand side network interface (eth1) of VM2 is connected to xenbr1, on port vif2.1. This ensures that the requests from users can reach it. The eth0 interface of VM2 is connected to vif2.0 port on xenbr0. |
| - | # It is important to note that the network 192.168.1.0/24 is invisible to the DSL router. Therefore, it is important to add a network route manually in the DSL router configuration, such as: Network 192.168.1.0/24 is reachable through this DSL router's LAN interface, using the gateway IP as 192.168.0.21 . | + | # Make sure that the network interfaces of the VMs get connected to correct bridges. The command <i>"brctl show"</i> can help you verify, which port is connected to which bridge. |
| - | # The reader might be thinking that the DHCPD running on VM1 (firewall) may be conflicting with the <i>dnsmasq</i> service running on this physical host. The reality is, that (a) dnsmasq | + | # VM2 (webcache) <i>can</i> connect to xenbr0 through its network interface on the left (eth0). (This is the debatable part mentioned in the previous point; the link connecting VM2's eth0 to xenbr0 is marked with a "*" for this purpose). If you want squid to get it's web pages from the internet, by going through VM1 (firewall), then there is no need to connect this link (marked with "*"). In this case, it would need to have it's GATEWAY set to the IP of VM1's eth1, which is 192.168.1.254 . However, remember, this introduces an extra hop for each web page request. i.e. A web request from a user will first land on VM1, (because it is the gateway for all users). From there the firewall rules will DNAT the traffic to VM2, as the firewall allows outgoing web requests only from the IP of VM2 (192.168.1.253). VM2 then sends the web request on the users behalf to the gateway, which allows it to go to the Internet and fetch the web page. However, if this link (marked with "*") is in place, then each time VM2 will get a user's web request, it can contact the internet <i>directly</i>, bypassing the firewall. One can argue that in this way security can be fooled, or firewall can be bypassed, if for example, a user sets his/her IP manually to the IP of VM2 (the cache server). However, certain protection mechanisms, such as turning off packet forwarding, and proper IPTables/firewall rules on the cache server, should be able to control this. |
| - | # When using XEN, the <i>libvirtd</i> service can be configured to be either turned | + | # It is important to note that the network 192.168.1.0/24 is invisible to the DSL router. Therefore, it is important to add a network route manually in the DSL router configuration, such as: <i>Network 192.168.1.0/24 is reachable through this DSL router's LAN interface, using the gateway IP as 192.168.0.21</i> . |
| + | # The reader might be thinking that the DHCPD running on VM1 (firewall) may be conflicting with the <i>dnsmasq</i> service running on this physical host. The reality is, that (a) dnsmasq is called internally from libvirtd service (b) by default dnsmasq only binds to virbr0 interface/192.168.122.1; and listens/serves VMs connected to this virtual bridge only. [Reference: http://permalink.gmane.org/gmane.comp.emulators.libvirt/21519] | ||
| + | # When using XEN, the <i>libvirtd</i> service can be safely configured to be either turned ON, or turned OFF. It is safe to let it remain turned on, even if you don't seem to be using it. The libvirtd service creates a private bridge, virbr0 and connects a private network to it (192.168.122.0/24), as shown in Figure 3. There is no harm in letting it do that. This may prove useful in test situations, where you may want to create a "private" virtual machine on the XEN host, such as VM3 and VM4 shown in the diagram. The dnsmasq service (run internally through libvirtd) has mechanism to service the DHCP, DNS requests of any virtual machines connected to this particular virtual private network. The libvirtd service also adds certain rules in the iptables firewall on the host system to provide NAT (MASQUERADE) services to virtual machines connected to virbr0, details of which are beyond the scope of this paper. | ||
| + | # VM3 and VM4 are the example private VMs. Each one of them has only one network interface card, connected to virbr0 on ports vif3.0 and vif4.0 respectively. | ||
===Configuration of Virtual Firewall System's components=== | ===Configuration of Virtual Firewall System's components=== | ||
| Line 112: | Line 144: | ||
* Physical Machine: Bare bone (text/minimal) installation of CENTOS 5.5, with XEN Hypervisor. [512MB RAM, 2 GB LVM slice for (/), 128 MB slice for swap] | * Physical Machine: Bare bone (text/minimal) installation of CENTOS 5.5, with XEN Hypervisor. [512MB RAM, 2 GB LVM slice for (/), 128 MB slice for swap] | ||
* VM1 (Firewall): Bare bone (text/minimal) installation of CENTOS 5.5, with IPTables. [ 128MB RAM, 1 GB LVM slice for (/), 64 MB slice for swap] | * VM1 (Firewall): Bare bone (text/minimal) installation of CENTOS 5.5, with IPTables. [ 128MB RAM, 1 GB LVM slice for (/), 64 MB slice for swap] | ||
| - | * VM2 (WebCache): Bare bone (text/minimal) installation of CENTOS 5.5, with IPTables, Squid, SquidGuard and optioanally SARG. [ 384MB RAM, 2-4 GB LVM slice for (/), 20GB - 30GB LVM slice for squid's cache directory, 64 MB slice for swap] | + | * VM2 (WebCache): Bare bone (text/minimal) installation of CENTOS 5.5, with IPTables, Squid, SquidGuard and optioanally SARG. [ 384MB RAM, 2-4 GB LVM slice for (/), 20GB - 30GB LVM slice for squid's cache directory, 64 MB slice for swap]. |
| + | |||
| + | <b>Note:</b> If you have more physical RAM, you should consider assigning extra RAM to the WebCache server (squid). This helps improve it's performance. | ||
===Configuration of Physical Machine=== | ===Configuration of Physical Machine=== | ||
| Line 118: | Line 152: | ||
* SSH allows key based authentication only. Direct root logins are dis-allowed. | * SSH allows key based authentication only. Direct root logins are dis-allowed. | ||
* Packet forwarding is <b>disabled</b> | * Packet forwarding is <b>disabled</b> | ||
| - | * The services xend (and libvirt) are configured to be accessed by the IPs from the right hand side LAN only. | + | * The services xend (and libvirt) are configured to be accessed by the IPs from the right hand side LAN only, 192.168.1.0/24. |
| - | * There are | + | * There are firewall/iptables rules on this machine, other than those used to protect it against attacks, such as ICMP ping floods, etc. Refer to the document: [Reference: http://cooker.techsnail.com/index.php/XEN,_KVM,_Libvirt_and_IPTables] |
| - | * The libvirtd service provides some extra rules in the physical host's iptables rules-set. It also sets up a private bridge (virbr0), with the network 192.168.122.0/24. | + | * The libvirtd service provides some extra rules in the physical host's iptables rules-set. It also sets up a private bridge (virbr0), with the network 192.168.122.0/24. On a XEN host, libvirtd service can be configured to be turned off, without any loss of functionality. |
| - | * The DNSMASQ service can be configured to be turned off using (chkconfig --del), however it would still be called internally from the libvirtd service. | + | * The DNSMASQ service can be configured to be turned off using (chkconfig --del), however it would still be called internally from the libvirtd service. Here is the dnsmasq process running under a user "nobody". (The line has been broken down into multiple lines to avoid horizontal scrolling): |
| - | * DNSMASQ service provides DHCP, DNS and NAT (Masquerade) services only to the virtual machines connected to virbr0. | + | <pre> |
| - | + | /usr/sbin/dnsmasq --strict-order --bind-interfaces --pid-file=/var/run/libvirt/network/default.pid \ | |
| + | --conf-file= --listen-address 192.168.122.1 --except-interface lo \ | ||
| + | --dhcp-range 192.168.122.2,192.168.122.254 --dhcp-lease-max=253 | ||
| + | </pre> | ||
| + | * DNSMASQ service provides DHCP, DNS and NAT (Masquerade) services only to the virtual machines connected to virbr0. If you do not have any VMs connected to the virbr0, it is better to stop/turn-off libvirtd and dnsmasq services. This will free up some resources on the physical host. | ||
===Configuration of VM1 (Firewall)=== | ===Configuration of VM1 (Firewall)=== | ||
* This machine does not run any service, other than SSH, and DHCPD. | * This machine does not run any service, other than SSH, and DHCPD. | ||
* IPTables rules are configured to filter (and redirect) traffic on various criteria, such as Source/Destination IP addresses and Ports, and packet state. | * IPTables rules are configured to filter (and redirect) traffic on various criteria, such as Source/Destination IP addresses and Ports, and packet state. | ||
| - | * Minimum number of IPTables rules, or efficient design of IPTables rules, as well as | + | * Minimum number of IPTables rules, or efficient design of IPTables rules, as well as turning off extra services, enable the firewall to work at peak performance. |
| - | * Packet forwarding is enabled | + | * Packet forwarding is enabled in either /etc/rc.local, or /etc/sysctl.conf file. |
* Certain TCP/IP kernel parameters can further be adjusted for performance gains. (optional) | * Certain TCP/IP kernel parameters can further be adjusted for performance gains. (optional) | ||
* There are no disk intensive operations on this VM. | * There are no disk intensive operations on this VM. | ||
| Line 138: | Line 176: | ||
* Packet forwarding is <b>disabled</b>. | * Packet forwarding is <b>disabled</b>. | ||
* Squid is the major disk I/O intensive process, running on this VM. | * Squid is the major disk I/O intensive process, running on this VM. | ||
| + | |||
| + | ==Conclusion== | ||
| + | Linux/Open-Source based firewalls are a great way to save money; while at the same time, not compromising on Security, Functionality or Efficiency. The virtualized Linux firewalls can save you from the hassle of installing a fresh Linux OS, and configuring it, each time you have a problem with the underlying hardware, or other types of breakdown. With Virtual Firewalls, you can start a saved (clone) image of your firewall on any other readily available hardware. They are also quite helpful, when you need multiple firewalls in your infrastructure. Copies of such Virtual Firewalls can instantly be created, adjusted, and put to work. Open-Source technology is what makes this easier, efficient and affordable! | ||
==Related Open Source Firewall Solutions== | ==Related Open Source Firewall Solutions== | ||
| - | If you are not confident in setting up your firewall | + | If you are not confident in setting up your firewall yourself, there are other alternatives, which you can safely use, in both non-virtualized and virtualized setups. These are: |
* Shorewall: http://www.shorewall.net/ | * Shorewall: http://www.shorewall.net/ | ||
* SmoothWall: http://www.smoothwall.org/ | * SmoothWall: http://www.smoothwall.org/ | ||
| Line 150: | Line 191: | ||
==References== | ==References== | ||
| - | * Cisco PIX | + | * Cisco PIX series : http://en.wikipedia.org/wiki/Cisco_PIX |
| + | * Cisco ASA 5500 series: http://en.wikipedia.org/wiki/Cisco_ASA | ||
* List of Open Source Firewalls and Routers: http://en.wikipedia.org/wiki/List_of_router_or_firewall_distributions | * List of Open Source Firewalls and Routers: http://en.wikipedia.org/wiki/List_of_router_or_firewall_distributions | ||
* XEN and the art of consolidation: http://www.shorewall.net/XenMyWay.html | * XEN and the art of consolidation: http://www.shorewall.net/XenMyWay.html | ||
Current revision as of 10:46, 4 April 2011
Alternate Titles: "Virtual Firewall Systems" Affordable and Robust Linux Firewalls
Author: Muhammad Kamran Azeem [CISSP, RHCE, OCP (DBA), CCNA] (http://wbitt.com , http://techsnail.com)
E-mail: kamran at wbitt dot com
Created: 08 March 2011
Updated: (Please see the footer area of this document for this information.)
Category: Virtualization, Security (Firewalls)
License: Copyright (c) 2011 by Muhammad Kamran Azeem. Permission to copy, distribute (sell or giveaway) and translate, provided you retain the name of the original author.
Synopsis: This paper discusses the concept of running your Linux Firewall as a Virtual Machine, and provides a design guide-line to do so.
Contents |
Introduction
In today's IT world, almost all IT managers know what exactly it means for the business, when a firewall is down. When this alarm is raised, it is just like the fire alarm. All of a sudden there is immense panic, there are question marks on everyone's face, productivity is halted, and people rush to see, who reaches to the coffee machine first; except the IT staff. To the IT staff, it seems like hell has broken loose. The managers of all level, almost all at once, start yelling at the IT staff, to get the network back up as soon as possible. It is quite a scene!
For people using hardware based firewalls of prominent brands, like Cisco PIX, Juniper NetScreen, or SonicWall, etc, this can actually mean a lot of downtime. Especially in cases when the firewall device has actually got burnt because of some power surge. They would have to wait for a replacement unit to arrive. In case the firewall was cracked, by a cracker, it would again mean a lot of downtime, as the firewall device has to be re-configured, probably from a clean backup, if there was any!
Normally there is only one such device in an environment, because they are pretty expensive. And, as noted above, a burnt device, or any component of it, such as a WAN port, can seriously cripple your business to a complete halt.
Many people consider Cisco PIX (Private Internet eXchange), as the Holy Grail of firewalls. Same is the general point of view about other hardware-based/proprietary firewalls, such as Juniper NetScreen, SonicWall, CheckPoint, NetGear, etc. There is nothing much you can do "different", with the so-called hardware/proprietary firewalls, compared to what you can do with Linux based firewalls. One of the popular strategy used by the sales people / vendors is to create Fear, Uncertainty and Doubt,(FUD), about low cost Linux firewalls, in the minds of customers. When they are successful in doing so, they (sales people) move to the next step, and convince their customers to purchase the ultra expensive firewall from brand X. The interesting point is, that even the IT managers at the customer side, do not resist in such purchases. Because, they "feel secure" by merely purchasing a branded product, and don't want to take any risk by saying "No". Once the brand X firewall product is acquired by the customer, it is placed on the network, without a well thought out configuration/plan. In a hurry to brag "I have configured the brand X firewall and placed it in production in 30 minutes", the IT staff, constantly under the influence of the brand X name/reputation, puts something on the network, which is, (a) not well configured, (b) no-body understands it well enough (c) is outrageously expensive, and (d) was not required in the first place. Most of the time it ends up like buying a rocket launcher to kill a fly.
In this paper we would discuss the possibility of using Linux based firewalls, running as both physical/hardware appliances; and as virtual machines, on a XEN / KVM host. We would also show, how this (firewall virtualization) can be achieved.
The Physical Firewall
The hardware-based branded firewalls
To explain this topic, we would use an example from the real world; the most commonly known firewall device, Ciso PIX. It would be interesting for many to know that the processors used in Cisco PIX firewalls were Intel Celeron, Intel PIII, and AMD's Am5x86. The chipsets used on the mainboards of these firewalls were Intel 440BX and AMD's SC520 chip-sets. And the RAM ranged between 16 MB to 512 MB (to 1 GB). [Reference: http://en.wikipedia.org/wiki/Cisco_PIX#Description_of_hardware].
Also, if you are thinking of buying any of the Cisco PIX firewall, you should note that in 2008 Cisco announced EOS (End of Sale) for Cisco PIX series. It is replaced with a newer "Adaptive Security Appliance", or ASA for short, introduced in 2005. Cisco ASA 5500 Series replaced three lines of Cisco security products: PIX, IPS and VPN. Models such as Cisco PIX 501 or Cisco PIX 515 are not produced or sold any more. Cisco PIX "technology" is still sold in a blade form, as a Firewall Services Module (FWSM) into Cisco's Catalyst 6500 Switches and 7600 Series Routers.
You can still purchase the older/used PIX devices/models for anywhere between $500 to $5000, depending on model, specifications, and of-course, the quality.
You would notice that even in newer Cisco security products (ASA 5500 series), the processors used are as low as 500 MHz and as high as 2.6 GHZ, with processor types including Intel P4, Celeron and AMD Opeteron. The medium range products in ASA 5500 series have RAM range between 256 MB and 1 GB. The higher end models have 4GB to 12 GB of RAM. [ Reference: http://en.wikipedia.org/wiki/Cisco_ASA]
The Cisco PIX firewall may been one of the best seller in the enterprise firewall areana, its ISO command line interface was never liked (and never fully understood) by the general (non-Cisco) IT staff. Same is almost true for all the branded/proprietary hardware firewalls out there.
Below are few more examples of hardware based firewalls:
- Netgear FVX538 Prosafe Dual WAN VPN FIREWALL WITH 8-PORT 10/100 SWITCH
- Processor: 533 MHz Intel XScale IXP425
- Memory: 32 MB flash, 64 MB DRAM
- Encryption accelerator: Cavium Processor up to 60+ Mbps (3DES+SHA-1) encryption
- Netgear FVS124G ProSafe Dual WAN VPN Gigabit Firewall
- Processor: 200 MHz 32-bit RISC
- Memory: 4MB Flash, 16MB DRAM
Most customers/users only look at the "initial" price of the firewall. In most of the cases, the hardware based firewalls from almost all prominent vendors provide limited services against the initial payment; and are sort of locked down to a small number of users/sessions/ports. These vendors charge extra, in the name of licenses, to allow more users traffic (sessions) to pass through the firewall. Normally the vendors also charge yearly subscription fee for premium services, such as Content Filtering, AntiVirus, AntiSpam, VPN, etc. This normally totals up to a larger sum, drawing out more money from the company, compared to what was anticipated in the beginning.
Readers might be wondering, "What is it, in a hardware appliance firewall, which makes is so costly?" The answer is, that the hardware firewalls have custom designed hardware. They may be using a standard Intel or AMD processor, but the other components would be built-in on the main-board. Network cards, which are the most important component/feature of a firewall device, are slimmed down, and are provided as network interfaces. There are also certain components, which you will not find in such an appliance. For example. You would not find a VGA, or Keyboard and mouse ports on your appliance. Such custom designs provide serial interfaces / console ports, which can be connected to using a null-modem cable, etc. You will find a minimum of two network ports on the most basic firewall. One for Internet (Red Zone), and the other for LAN (Green zone). The newer designs include several network ports; some of them are additionally there to provide facility to configure DMZs (Orange Zone). Also, the newer firewalls devices/appliances have built in Wireless device, providing a fourth configurable zone (Blue Zone). Instead of using a hard disk for storage, you will find small sized flash disks. The OS is proprietary with a minimal user interface, normally through command line. In newer designs, firewall vendors have started providing secure web interface to configure the device. The operating system is minimalistic in nature, and does not consume much RAM too. It therefore does not "require" extra RAM to function. And above all, all components are enclosed in a small (slick) box, which does not take up much desk/rack space. This all is what makes such devices known as "hardware based firewalls" or "branded firewalls".
The hardware-based Linux firewalls
Fundamentally, any hardware-based firewall is a collection of hardware and software components. A hardened Linux box, with enough resources, used "solely" in a firewall role, can confidently be termed as a hardware firewall; and it can compete with any branded firewall you can throw against it. Besides, it is the configuration, which makes a firewall strong; not it's brand.
A modern day PC is much more powerful than what is described above. A cut down version / minimal install of Linux OS of your choice, on a commodity off the self (COTS) PC, can essentially turn it into a firewall, more powerful than the Cisco PIX. The only (non-serious) disadvantage may be the dimensions of your Linux box. The physical dimensions of an ordinary desktop computer takes up a lot of space on the desk, floor or rack. (It may look ugly too!).
Linux and its command line interface is very well understood by almost all Open Source enthusiasts. Plus, there is a lot of documentation/help out there on the Internet. Thus, using Linux as the OS for your firewall proves to be an excellent choice. Linux OS is normally available free of cost, so the only direct costs are the hardware costs for such a firewall. The cost of a custom made (Linux) firewall device, range between $200-$900, depending on your requirements. Still it is much lower a price compared to $5000+ for a branded firewall. A Linux based hardware firewall can offer almost all services which any other type of firewall can offer. It is just the matter of adding the right modules and software pieces to it. For example, a basic Packet Filtering Linux Firewall can work as a Stateful Firewall, merely by adding a connection tracking kernel module, and some configuration. The following non-exhaustive list provides an insight into what all can be accomplished by using Linux OS and it's free tools.
- Packet Filtering: IPTables
- NAT: NAT module in IPTables
- Stateful Filtering: Connection Tracking module in IPTables
- Web Proxy/Caching Service: Squid, etc.
- Web Content Filtering: SquidGuard, DansGuardian, etc.
- Anti Virus: CLAMAV, etc.
- Anti SPAM: Spamassassin, etc.
- VPN: OpenVPN, OpenSWAN, etc.
- Intrusion Detection Systems: Snort, etc.
- Network Monitoring and Alerting: MRTG, MON, Nagios, ganglia, etc.
- An SMTP relay: Sendmail, Postfix, etc.
- .... and more.
You can have one "thick" Linux firewall, in your network, by having all of the security services on one physical machine, which is an advantage in it's own. (You will not experience virtualization overheads, explained later). There are many Open Source firewall projects, which are reliable and robust; and are being used in production networks all over the world. Shorewall, SmoothWall, Untangle, Endian, IPCop, CopFilter and pfSense are few excellent firewall solutions , usable in environments ranging from SOHO, to enterprise.
To give you an idea of the hardware, and related costs, consider a normal PC, with P4 or higher processor, 800 MHz or higher speed, 256 MB or more RAM, and 40 GB or more disk space, with at least 2 Network cards. A PC with such hardware specifications is an ideal candidate for a firewall device/appliance. 800 MHz processor is good enough to handle about 50 users. The more users you have, the more powerful processor you need, (along more RAM), because the primary function of any firewall (packet filtering), eats the most of the CPU. If you also need to provide VPN, you should consider a processor with speed in excess of 1.6 GHz. As noted above, the cost of such custom made (Linux) firewall device, range between $200-$900, depending on your requirements. Again, it is much lower a price compared to $5000+ for a branded firewall.
Note: While power is a concern for any equipment you are running, don't fall into the trap of using Atom processors, just for the reason that they consume low power. Atom processors do not have enough compute power to act as an efficient firewall for a larger network.
While this paper is about Virtualizing your firewalls, make no mistake in understanding that a physical/hardware firewall, will always outperform a virtual one. This is because there are no virtualization overheads, nor any infrastructure complexities. If you can afford the cost of extra hardware, the power consumption, and the configuration time, we recommend that you use a physical (Linux) firewall instead of setting up a virtual one. It is highly recommended to have redundancy of the equipment, to provide business continuity. Linux firewalls are very efficient and secure, (if configured correctly), economical, and affordable, compared to their branded counter parts. There is no reason, why you should not use one.
The Virtual Firewall
In this paper, we try to explain, how compartmentalized security model can be implemented, by running most of the services listed above as separate "thin" virtual machines, on a single physical server. And that for the sake of ensuring business continuity, a copy of all VMs can be kept on a second (in-expensive) physical machine. In case of hardware failure, the firewall and it's related components can be run from this second machine, without significant downtime.
Thus, instead of running one "thick" physical machine as firewall, we can run multiple "thin" virtual machines. Below are few of advantages and disadvantages of running your firewall as a VM.
Advantages
- Compartmentalized Security: One VM can be setup to act as a firewall, while the other VM can run services like WebCache, DNS, etc. If a cracker gains access to the cache server, that is the only VM affected. Your main firewall will still continue to handle traffic.
- No single point of failure: If one VM's disk is full, with logs, etc, it will be the only VM, which will fail, or will not respond. The other VM will keep functioning.
- Service/VM Load Balancing: If the VM running the WebCache/content-filtering services is taking too much physical resources of the physical host, that VM can be moved to another physical machine on the network.
- COTS/in-expensive hardware: This gives you the (financial) freedom to have multiple physical machines in stock. In case a hardware failure occurs, the second physical machine can be quickly setup to run these VMs and the services they offer.
- Cloud capable: Virtual firewalls can prove really useful in environments which are heavily virtualized, such as Cloud. Several virtual firewalls can exist within a larger virtual network, serving different departments, or different customers.
- Support: Normally, the first question asked about a product, before it's formal review is: "Who will provide support for this?" . In case of the in-expensive Linux firewalls (both Physical and Virtual), explained in this paper, the support is expected from the particular distribution vendor who's Linux flavour is installed on the firewall. This is true for almost all commercial Linux distributions. However, if you are running free distributions, such as Debian, CENTOS, Fedora, Ubuntu, etc; you should expect the support from your Linux administrators. In 99% of cases, it is the Linux system admins in the IT staff, who propose, and often implement such technologies without external help. As you would be noticing that the free Linux distributions cannot be directly asked to provide support. However, they all have bug tracking / issue tracking systems, which are actively monitored by the back end developers. Also, there are "support companies" active in this field, who provide commercial/professional support for these free Linux distributions.
Disadvantages
- Virtualization overhead: Virtualization means, that there must be a Hypervisor, to host all virtual machines. The hypervisor itself consumes certain amount of resources, mainly RAM, and CPU. If the size of RAM is already low/small on the physical host, there is little left for VMs to run efficiently. This is equally true for any computer system which is low on CPU power, and in some cases, disk-space.
- Extra complexity: Virtualization introduces extra level of complexity in the infrastructure/network. The administrator has not only to take care of the physical machine and it's network connections, for example; he also has to take care of the VMs, the virtual networks inside the machine, and a keep an eye on the resource utilization.
- Requirement of additional IPs: All virtual and physical network interfaces (of physical and virtual machines) need to have IPs assigned to them. Thus there is a requirement of additional IPs.
Note: If you do not plan to host many thin VMs on your physical host, or if you are low on hardware resources, you can simply let go of the idea of Virtualizing your firewall, and just go ahead with a physical (Linux based) firewall. One of the key principals of security is to keep your system "managed" and "manageable". The moment the complexity of any system becomes un-manageable, it develops vulnerabilities, which can later be exploited. Thus, simplicity must be a fundamental idea when designing any system; and firewalls are not an exception.
Designing a Virtual Firewall System
Scenario
While designing a Virtual Firewall System, and it's components, you should first identify the tasks it will be performing for your network. In this document, we have the assumption, that you are placing such a firewall between Internet and your LAN users, to protect them from each other. Internet is reachable through a DSL router, which has a public IP. The LAN interface of this DSL router is connected to a switch, to which all of your users are connected to. The DSL router, is providing DHCP, DNS and NAT services to your users. We will also assume that the DSL Router has a built-in firewall, which no-one has bothered to configure for your setup, or has very limited firewall features. The users need to be protected (from the Internet), and also provided with some basic services, such as a cache server. The Internet needs to be protected from the LAN users, such as, any virus infected PC should not send floods of emails/spam through your DSL router, towards the internet. Thus a need to place a Linux firewall in between. First, here is how the setup looks like when there is no firewall placed on the network.
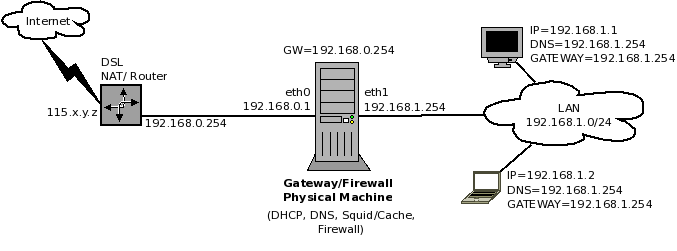
Here is what a non-virtualized "thick" solution looks like:
The Proposed Solution: Virtual Firewall System
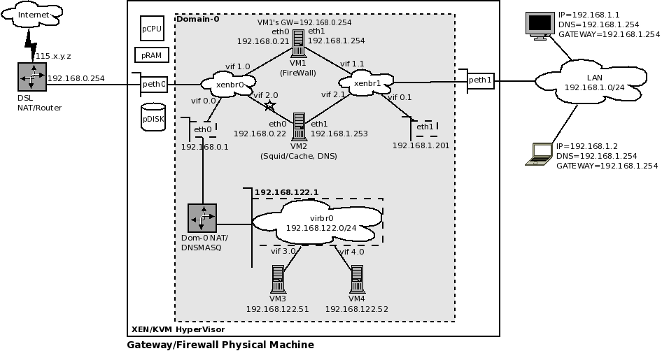
We have used XEN as an example to create a Virtual Firewall System. The design is shown in the diagram below. You can also use KVM, if you want to.
Larger version of this diagram is available at: http://cooker.techsnail.com/images/d/dd/Firewall-Virtualization-03.png
The diagram is explained as following:
- The physical/gateway/firewall machine shown in Figure 2, in the previous section, has been replaced by a large box.
- peth0 and peth1 are the physical network cards of the physical machine.
- pCPU = Physical CPU, pRAM = Physical RAM, and pDISK = Physical Disk
- The grey box inside the big white box is supposed to be Domain-0. In a perfect diagram, all virtual machines should be drawn outside the grey box. You can still assume the grey box to be Domain-0 for ease of understanding. For better understanding of this point, check the XEN network concepts explained in this article: [Reference: http://cooker.techsnail.com/index.php/Virtualization-XEN]
- xenbr0 is a software bridge, connected to the physical LAN 192.168.0.0/24, through peth0. The virtual network card eth0 of Domain-0 (XEN host) is connected to this bridge on port vif0.0 .
- xenbr1 is a software bridge, connected to the physical LAN 192.168.1.0/24, through peth1. The virtual network card eth1 of Domain-0 (XEN host) is connected to this bridge on port vif0.1 .
- VM1 is XEN Domain-1 (dom-U), and is configured to act as a firewall.
- VM2 is XEN Domain-2 (dom-U), and is configured to run WebCache (squid), and DNS (BIND) services.
- Notice the change in IP assignment in Figure 3, compared to Figure 2. The IP used as GATEWAY by the LAN users, is now assigned to eth1 of VM1 (firewall), instead of eth1 of the physical host.
- VM1 runs in the Firewall role. It has two interfaces, each connecting to a different bridge, (xenbr0 and xenbr1), and thus essentially becomes/acts-as a router. The eth0 interface of VM1 is connected to vif1.0 port on xenbr0. The eth1 interface of VM1 is connected to vif1.1 port on xenbr1. VM1 runs DHCPD service listening/serving on it's eth1 interface.
- VM2 runs in the WebCache role, and also provides caching DNS services, using BIND (caching-nameserver). It is running Squid on port 3128. It also has two interfaces(, which may be debatable). The right hand side network interface (eth1) of VM2 is connected to xenbr1, on port vif2.1. This ensures that the requests from users can reach it. The eth0 interface of VM2 is connected to vif2.0 port on xenbr0.
- Make sure that the network interfaces of the VMs get connected to correct bridges. The command "brctl show" can help you verify, which port is connected to which bridge.
- VM2 (webcache) can connect to xenbr0 through its network interface on the left (eth0). (This is the debatable part mentioned in the previous point; the link connecting VM2's eth0 to xenbr0 is marked with a "*" for this purpose). If you want squid to get it's web pages from the internet, by going through VM1 (firewall), then there is no need to connect this link (marked with "*"). In this case, it would need to have it's GATEWAY set to the IP of VM1's eth1, which is 192.168.1.254 . However, remember, this introduces an extra hop for each web page request. i.e. A web request from a user will first land on VM1, (because it is the gateway for all users). From there the firewall rules will DNAT the traffic to VM2, as the firewall allows outgoing web requests only from the IP of VM2 (192.168.1.253). VM2 then sends the web request on the users behalf to the gateway, which allows it to go to the Internet and fetch the web page. However, if this link (marked with "*") is in place, then each time VM2 will get a user's web request, it can contact the internet directly, bypassing the firewall. One can argue that in this way security can be fooled, or firewall can be bypassed, if for example, a user sets his/her IP manually to the IP of VM2 (the cache server). However, certain protection mechanisms, such as turning off packet forwarding, and proper IPTables/firewall rules on the cache server, should be able to control this.
- It is important to note that the network 192.168.1.0/24 is invisible to the DSL router. Therefore, it is important to add a network route manually in the DSL router configuration, such as: Network 192.168.1.0/24 is reachable through this DSL router's LAN interface, using the gateway IP as 192.168.0.21 .
- The reader might be thinking that the DHCPD running on VM1 (firewall) may be conflicting with the dnsmasq service running on this physical host. The reality is, that (a) dnsmasq is called internally from libvirtd service (b) by default dnsmasq only binds to virbr0 interface/192.168.122.1; and listens/serves VMs connected to this virtual bridge only. [Reference: http://permalink.gmane.org/gmane.comp.emulators.libvirt/21519]
- When using XEN, the libvirtd service can be safely configured to be either turned ON, or turned OFF. It is safe to let it remain turned on, even if you don't seem to be using it. The libvirtd service creates a private bridge, virbr0 and connects a private network to it (192.168.122.0/24), as shown in Figure 3. There is no harm in letting it do that. This may prove useful in test situations, where you may want to create a "private" virtual machine on the XEN host, such as VM3 and VM4 shown in the diagram. The dnsmasq service (run internally through libvirtd) has mechanism to service the DHCP, DNS requests of any virtual machines connected to this particular virtual private network. The libvirtd service also adds certain rules in the iptables firewall on the host system to provide NAT (MASQUERADE) services to virtual machines connected to virbr0, details of which are beyond the scope of this paper.
- VM3 and VM4 are the example private VMs. Each one of them has only one network interface card, connected to virbr0 on ports vif3.0 and vif4.0 respectively.
Configuration of Virtual Firewall System's components
The configuration of the components is not a big science. There is nothing to be afraid of. We have one physical server, with two physical interface cards, and two VMs running inside it. We would recommend at least 1 GB of physical RAM and 2.x GHz Intel P4 (or higher), or an AMD Athlon XP processor (or higher). The physical disk size depends on your requirement, and the amount of software you are going to install. We would recommend you to use LVM on the disk, on the host OS, so you can add and remove virtual disks easily. It is also easy to resize disks this way. Below is an example breakdown of the machines, in terms of RAM and Disk requirements.
- Physical Machine: Bare bone (text/minimal) installation of CENTOS 5.5, with XEN Hypervisor. [512MB RAM, 2 GB LVM slice for (/), 128 MB slice for swap]
- VM1 (Firewall): Bare bone (text/minimal) installation of CENTOS 5.5, with IPTables. [ 128MB RAM, 1 GB LVM slice for (/), 64 MB slice for swap]
- VM2 (WebCache): Bare bone (text/minimal) installation of CENTOS 5.5, with IPTables, Squid, SquidGuard and optioanally SARG. [ 384MB RAM, 2-4 GB LVM slice for (/), 20GB - 30GB LVM slice for squid's cache directory, 64 MB slice for swap].
Note: If you have more physical RAM, you should consider assigning extra RAM to the WebCache server (squid). This helps improve it's performance.
Configuration of Physical Machine
- Physical machine "does not" run any service, other than the following: SSH, xend, libvirt (optional).
- SSH allows key based authentication only. Direct root logins are dis-allowed.
- Packet forwarding is disabled
- The services xend (and libvirt) are configured to be accessed by the IPs from the right hand side LAN only, 192.168.1.0/24.
- There are firewall/iptables rules on this machine, other than those used to protect it against attacks, such as ICMP ping floods, etc. Refer to the document: [Reference: http://cooker.techsnail.com/index.php/XEN,_KVM,_Libvirt_and_IPTables]
- The libvirtd service provides some extra rules in the physical host's iptables rules-set. It also sets up a private bridge (virbr0), with the network 192.168.122.0/24. On a XEN host, libvirtd service can be configured to be turned off, without any loss of functionality.
- The DNSMASQ service can be configured to be turned off using (chkconfig --del), however it would still be called internally from the libvirtd service. Here is the dnsmasq process running under a user "nobody". (The line has been broken down into multiple lines to avoid horizontal scrolling):
/usr/sbin/dnsmasq --strict-order --bind-interfaces --pid-file=/var/run/libvirt/network/default.pid \ --conf-file= --listen-address 192.168.122.1 --except-interface lo \ --dhcp-range 192.168.122.2,192.168.122.254 --dhcp-lease-max=253
- DNSMASQ service provides DHCP, DNS and NAT (Masquerade) services only to the virtual machines connected to virbr0. If you do not have any VMs connected to the virbr0, it is better to stop/turn-off libvirtd and dnsmasq services. This will free up some resources on the physical host.
Configuration of VM1 (Firewall)
- This machine does not run any service, other than SSH, and DHCPD.
- IPTables rules are configured to filter (and redirect) traffic on various criteria, such as Source/Destination IP addresses and Ports, and packet state.
- Minimum number of IPTables rules, or efficient design of IPTables rules, as well as turning off extra services, enable the firewall to work at peak performance.
- Packet forwarding is enabled in either /etc/rc.local, or /etc/sysctl.conf file.
- Certain TCP/IP kernel parameters can further be adjusted for performance gains. (optional)
- There are no disk intensive operations on this VM.
Configuration of VM2 (WebCache)
- This machine does not run any services, except: SSH, squid, SMTP Relay (PostFix), and DNS (BIND/caching-nameserver).
- Squid is only accessible from the right hand side LAN (192.168.1.0/24).
- Packet forwarding is disabled.
- Squid is the major disk I/O intensive process, running on this VM.
Conclusion
Linux/Open-Source based firewalls are a great way to save money; while at the same time, not compromising on Security, Functionality or Efficiency. The virtualized Linux firewalls can save you from the hassle of installing a fresh Linux OS, and configuring it, each time you have a problem with the underlying hardware, or other types of breakdown. With Virtual Firewalls, you can start a saved (clone) image of your firewall on any other readily available hardware. They are also quite helpful, when you need multiple firewalls in your infrastructure. Copies of such Virtual Firewalls can instantly be created, adjusted, and put to work. Open-Source technology is what makes this easier, efficient and affordable!
Related Open Source Firewall Solutions
If you are not confident in setting up your firewall yourself, there are other alternatives, which you can safely use, in both non-virtualized and virtualized setups. These are:
- Shorewall: http://www.shorewall.net/
- SmoothWall: http://www.smoothwall.org/
- Untangle: http://www.untangle.com/
- Endian: http://www.endian.com/en/community/overview/
- IPCop: http://www.ipcop.org/
- CopFilter (IPCop add-on): http://www.copfilter.org/
- pfSense: http://www.pfsense.org/
References
- Cisco PIX series : http://en.wikipedia.org/wiki/Cisco_PIX
- Cisco ASA 5500 series: http://en.wikipedia.org/wiki/Cisco_ASA
- List of Open Source Firewalls and Routers: http://en.wikipedia.org/wiki/List_of_router_or_firewall_distributions
- XEN and the art of consolidation: http://www.shorewall.net/XenMyWay.html
- Adding additional network bridge for eth1: http://idolinux.blogspot.com/2008/08/xen-add-network-bridge-for-eth1.html
- Using multiple network cards in XEN: http://www.debian-administration.org/articles/470
- libvirt/dnsmasq integration: http://permalink.gmane.org/gmane.comp.emulators.libvirt/21519
- Trouble Shooting DHCP: http://debianclusters.org/index.php/Troubleshooting_DHCP
- Trouble Shooting DHCP: http://www.ixiacom.com/library/test_plans/display?skey=dhcp-server
- Xen starting dnsmasq?: http://markmail.org/message/ydcl62pp62plyb6r
- http://cooker.techsnail.com/index.php/Virtualization-XEN
- http://cooker.techsnail.com/index.php/XEN,_KVM,_Libvirt_and_IPTables